Inconsistent Behavior When Deleting HSM Certificates on the Security Server
Introduction
Sometimes, due to how internal caching works, HSM keys and certs can behave in an inconsistent manner.
Step 1
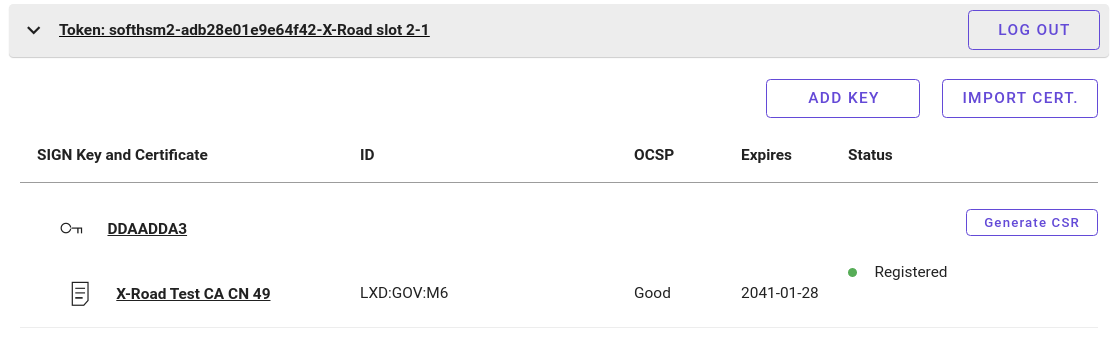
This example starts with a HSM token that contains key DDAADDA3 and associated signing certificate X-Road Test CA CN 49 for member LXD:GOV:M6.
Certificate has been imported from the HSM token.
Step 2
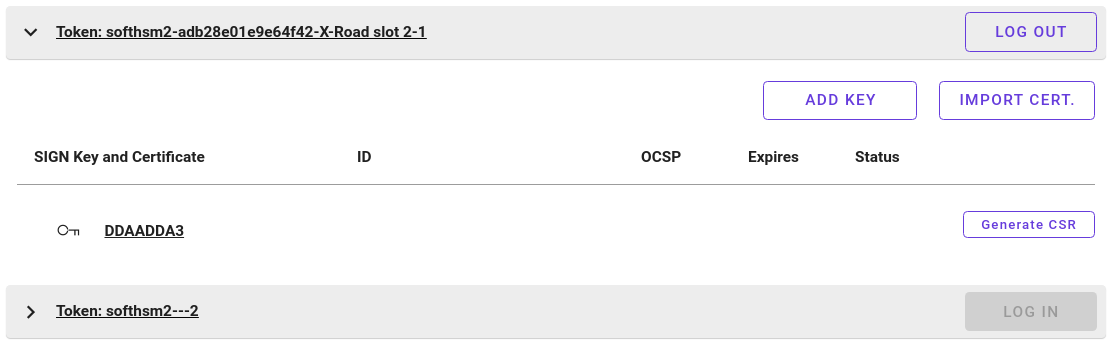
Next, the signing certificate is deleted from Security Server. This removes the certificate from Security Server configuration, but does not modify contents of HSM.
Immediately after clicking on delete, certificate seems to have disappeared. The key is still visible under SIGN Key and Certificate.
Step 3
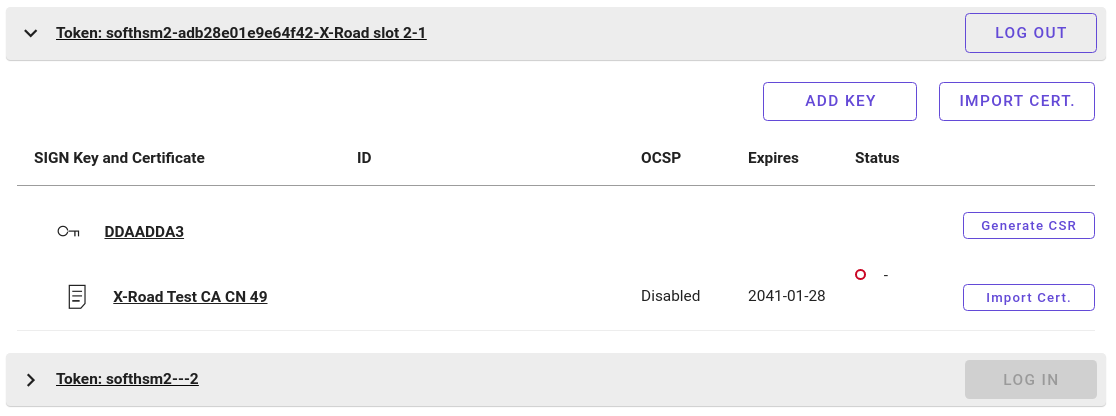
Waiting for a moment (a minute or so) makes certificate reappear. Now it has status "Deleted", indicated by a red circle and a hyphen.
Difference between steps 2 and 3 is explained by internal caches, which have not yet updated in step 2.
UI still retains the knowledge of the fact that this is a sign key and certificate.
Step 4
Next, signer process is restarted, e.g. with
systemctl restart xroad-signer
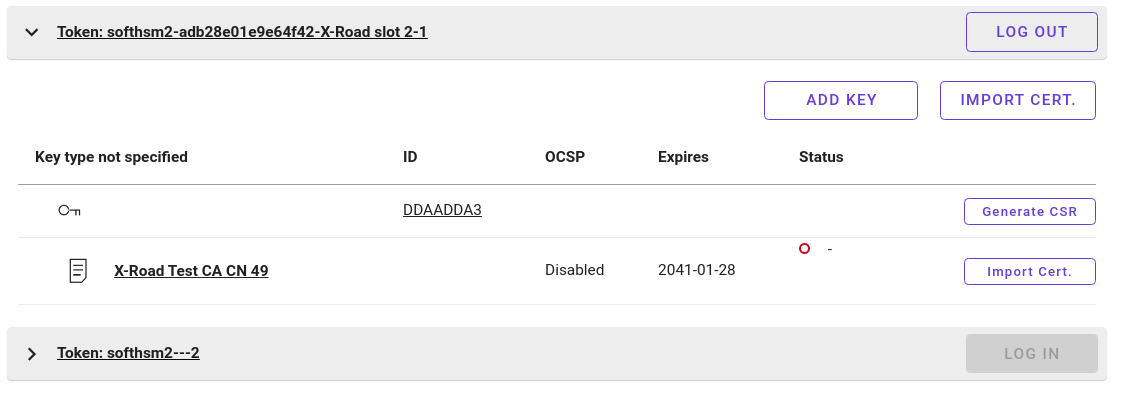
After signed restart, the key and certificate appear under category Key type not specified.
Explanation
This behavior is caused by internal caches, that do not correctly represent the persistent state of HSM key and certificate after deletion, until signer process has been restarted.
After the certificate has been deleted, Security Server has only transient knowledge of the key and certificate type (signing). After restart, this transient information disappears.
Inconsistencies in displaying the keys and certificates can lead to unexpected behavior. Usually deleting a certificate from SIGN Key and Certificate category removes the certificate from Security Server configuration, but does not modify HSM contents. However, deleting the certificate in step 3 is possible, and will delete it from HSM.
A signer restart (on step 4) may be useful, if HSM keys and certs seem to behave weirdly.
Related articles